Identity theft
Computer and identity theft—what you don’t know will hurt you
“Someone got my credit card.”A very simple statement. Nothing I expected from my sister while we were running around the mall doing some holiday shopping. When I asked her how she knew, she said her husband noticed some Yahoo charges over the past month. That wasn’t the worst - she also had a credit check listed. How much information can be gleaned from one credit check, especially in the wrong hands? Unfortunately, this is not a stand-alone case. It happens more often than we realize. With our world of immediate access and possible innumerable breaches of our private personal information, it is a miracle that anything is safe.
What they want
• Name
• Date of birth
• Address
• Telephone numbers
• Driver's license
• Credit card account numbers
• Bank account numbers
• Social Security number
How they get it
• Dumpster diving (the thief goes through the victim's trash looking for discarded personal information or unwanted preapproved credit offers).
• Stealing incoming and outgoing mail.
• Stealing a wallet or purse.
• Shoulder surfing (the thief watches what PIN number is input into an ATM machine).
• If you keep information such as your income taxes or account numbers on your PC, a hacker may be able to extract that data from your system.
• A disgruntled employee may sell personal information to a thief.
It must be a family thing, because something similar happened to me. Prior to the use of NCR credit forms, the only problem with identity theft was the misuse of a charge card. I remember receiving a phone call one summer, many years ago. It was Visa, asking me if I had been to Brazil recently. I had said, no, but apparently my charge card did. Someone had taken the carbon of the credit card copy (my best guess was it occurred while I was at an international tennis tournament in Miami), and spent oodles of dollars, including mucho diniro at a dental office! The irony did not escape me. The good news: Visa said I was not responsible for these charges. The bad news: The problem still goes on.
Identity theft is one of the biggest personal safety issues of our time. Identity theft, in addition to consumer fraud, affects millions of unsuspecting people each year.
They are having their privacy invaded in a very personal manner. According to the Identity Theft Protection Information and Resource Center, “Every 79 seconds someone becomes a victim of identity theft. One in 23 Americans will be victims this year. And the costs are high. The Federal Trade Commission estimates the price tag of identity theft to be $52.6 billion dollars. Those are horrifying statistics.
HIPAA is trying to protect personal private health information. With all the laws in place to prevent unwanted access to medical records, one corner of our lives is, in theory, secure. What about the rest of our information? Our Social Security numbers? Our bank accounts? Our passwords? What is happening out there is enough to say you will never sign up for a free television in the mall, an email list for recipes, or subscribe to a magazine. You have no idea what information is out there, being shared, how it is disseminated, and by whom. Not to mention, who is receiving all this personal stuff (Table 1).
Identity theft occurs every day. Apparently, it is incredibly easy. In 2001, 42 percent of all consumer complaints to the Federal Trade Commission were from identity theft victims. From rummaging through the trash cans, finding an unused credit card application, to a disgruntled employee giving away that credit card you so trustingly allowed him/her to use, it occurs at an alarming rate. The thieves use this information to buy cars, computers, real estate, whatever they please. They establish their own credit with your funding. You have seen the commercials on television. The biker guy in a spa. They are meant to amuse but the scenario is very real (Table 2).
The main method of obtaining personal information is still the old-fashioned way: theft of wallets, mail, and friends and relatives. According to the Better Business Bureau, computer identity theft is a small percentage (11.6 percent) of the total crimes committed. The crime is more often committed less esoterically. Aside from the apparent bad guys rummaging through your garbage cans or pilfering a credit card application from your outside mailbox, things do go missing in private homes. We tend to lower our personal radar in our own house and leave private materials on kitchen counters, dining room buffets, or even living room tables. Half of the identity theft criminals are friends, relatives, and in-home employees of the victim.
What about the other half? According to Ray Williams, a former detective from the Lincolnwood Police Department, a more recent trick that is being used is to grab information from people in public places. The bad guys are using the newer cell phones that have motion picture capture capabilities and pointing them at unsuspecting people using public phones to record passwords of calling cards as they are tapped onto the phone keypad. You can only begin to imagine what a creative mind is capable of with the camera phones. Yes, hackers are out there. They do get your passwords, but some are not sitting at their computers, trying to discover number and letter permutations.
Did you realize you could have your identity silently zipped off during a dining experience? After a meal in a restaurant, we think nothing of tossing our credit card down on the table to pay the bill. Once we give our card, the server heads over to the register to charge our meal. But, there is a small hand-held machine called a skimmer. This device takes only a few seconds to scan the magnetic strip on the back of the credit card. The strip contains all personal data, such as name, address, credit limit, and personal identification number. The entire process takes seconds. The information is then used to create new, duplicate credit cards. Unfortunately, there is no way to determine if your credit card has been skimmed, so it is prudent to check your statements with due diligence each month.
Here is a frightening concept. Imagine just doing your normal business and having your cell phone’s database hacked into? In Europe, Bluetooth subscribers were prey to a virus that scanned data from their cell phones and retrieved them into a laptop. Sound crazy? The system used is a simple one that will allow cell phones, computers, and other digital devices to “talk to each other.” Cell phones now are so advanced they function as multicommunication devices. The program, called “bluesnarfing,” is able to copy addresses, photos, calendars, anything the person has stored on his phone. Some of these cell phones have credit card information stored to purchase small items, similar to the pass cards at your local McDonald’s. The problem lies in the fact the Bluetooth system is continuously “on” so, therefore, it is always vulnerable.
Cell phones can also be taken over in a system called “bluebugging.” The phones may be completely taken over by another phone, without the person having any knowledge of the situation. When one phone rings, the thief’s phone also rings. Any and all conversations may be heard. This is a perfect tool for corporate spies. Again, the address book and contact list may be rewritten, but it takes a more difficult connection between cell phones to establish.
Hacking has become downright creative. “Phreakers,” as they are called, find ways to send out a different caller id number after stealing it from a victim. Calling the cell phone company and notifying them that they wanted to have their cell phone connected to their computer, a connection was established. Unbeknownst to the Internet phone company, the number was another person’s cell phone. But, with that new fraudulent number, access to personal banking accounts and ATM is now open wide and new credit cards can be created, not to mention a new bank account with the victim’s money.
It may not be only on the home front that we have to be aware. Vacation is another time we may be at personal risk. Our personal warning defenses may be down, as we are in “relax mode.” It may not be the obvious: your wallet gone missing from a pocket or purse. As my personal experience testifies, once that credit card receipt is gone, you truly have no control over where it goes. Some establishments still list the entire credit card number on all receipts. A few vacation tips: if you are gone for a long time, have your home mail held at the post office, carry a minimal number of checks and credit cards, and apply all due diligence regarding personal information lying around the hotel room. Consider making a list of any personal identification pieces (passport, credit cards, and insurance cards) that you are bringing with you and leave a copy at home, in a safe place.
Identity theft is a federal and state crime. There are several laws on the books protecting citizens. The Identity Theft and Deterrence Act of 1998 is also known as the identity theft act, making it a federal crime to steal someone’s identity (www.ftc.gov/os/statutes/itada/itadact.htm). If your identity has been stolen, the Fair Credit Reporting Act will allow for a correction to a credit report (www.ftc.gov/os/statutes/fcra.htm). Electronic banking transactions are protected through the Electronic Funds Transfer Act. Lost or stolen ATM or debit cards are not liable to more than $50, if reported prior to unauthorized use (www.ftc.gov/bcp/conline/pubs/credit/elbank.htm). The Fair Credit Card Billing Act protects the consumers from billing errors.
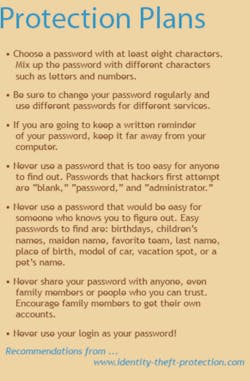
But what can we do to be proactive in protecting our identity? Purchasing a shredder, for both your personal home and business, is a small piece of insurance. Any and all charge card applications that you have no interest in keeping should be shredded. Requesting copies of your personal credit history, at nominal costs, should be done on a routine basis. Frequent checking of online credit card and bank accounts is a must, especially if any of those have electronic access. By calling (888) 5-OPTOUT - (888) 567-8688 - you can opt out of receiving those annoying applications for every credit card under the sun. By contacting The Direct Marketing Association Mail Preference Service, you can remove your name from direct mailing lists (www.the-dma.org).
What happens if you are a victim? The Federal Trade Commission’s Web site, www.consumer.gov/idtheft/, is where Ray Williams sends many of the victims he has dealt with. It lists what a victim should do and who to call after discovering a problem. This is an excellent resource.
Your identity is a very important piece of your life. If someone takes this personal information from you, your life may be irrevocably altered. You are a victim of a federal crime. Being proactive will protect this valuable personal asset. If you do become a victim, report it immediately. Getting your life back together is key. Not allowing a theft to happen in the first place is crucial. There is so much at stake.
The author wishes to thank Mr. Ray Williams, Lincolnwood Police Department 911 Coordinator and Police Network Administrator, and Mr. Guy Ballard, director of technology, Niles Township High School District 219, Skokie, Ill., for their invaluable experience and assistance.
Sheri B. Doniger, DDS, has been in the private practice of family and preventive dentistry for more than 20 years. A dental hygiene graduate of Loyola University prior to receiving her dental degree, her current passion is focusing on women’s health and well-being issues. She may be contacted at (847) 677-1101 or [email protected].
References
Federal Trade Commission, www.consumer.gov/idtheft, accessed May 31, 2004
Privacy Rights Clearinghouse, www.privacyrights.org/identity.htm, accessed May 31, 2004
Identity Theft: Prevention and Survival, www.identitytheft.org, accessed May 31, 2004
Identity Theft and Fraud: Department of Justice, www.usdoj.gov/criminal/fraud/idtheft.html, accessed May 31, 2004
Identity Theft Protection Information & Resource Center, www.identity-theft-protection.com, accessed Jan. 15, 2005
“They’ve Got Your Number” Wired Magazine, Dec. 2004, www.wired.com/wired/archive/12.12/phreakers.html, accessed Dec. 20, 2004